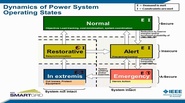
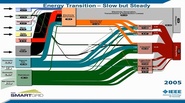
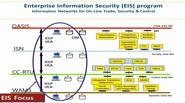
372 resources related to
Security Management
Read more
Featured Article
Read more
Related topics
No topics related to "Security Management"
Top Conferences on Security Management
2022 IEEE International Carnahan Conference on Security Technology (ICCST)
2021 IEEE International Conference on Systems, Man, and Cybernetics (SMC)
2021 IEEE International Professional Communication Conference (ProComm)
2020 IEEE 23rd International Conference on Computational Science and Engineering (CSE)
2020 International Conference on Electrical Engineering (ICEE)
2020 IEEE 14th International Conference on Application of Information and Communication Technologies (AICT)
2020 International Conference on Machine Learning and Cybernetics (ICMLC)
2020 IEEE International Conference on Intelligence and Security Informatics (ISI)
2020 IEEE 41st Sarnoff Symposium
2020 IEEE International Conference on Power Systems Technology (POWERCON)
2018 9th International Conference on Information Technology in Medicine and Education (ITME)
2018 13th World Congress on Intelligent Control and Automation (WCICA)
2018 25th International Conference on Systems, Signals and Image Processing (IWSSIP)
2018 12th International Conference on Reliability, Maintainability, and Safety (ICRMS)
2016 6th IEEE International Conference on Broadband Network & Multimedia Technology (IC-BNMT)
2012 International Conference on Management and Service Science (MASS 2012)
2012 International Conference on Information Systems for Crisis Response and Management (ISCRAM-ASIA)
2012 IEEE 3rd International Conference on Emergency Management and Management Sciences (ICEMMS)
2011 3rd International Conference on E-business and Information System Security (EBISS)
2011 2nd International Conference on Financial Theory and Engineering (ICFTE)
2011 6th International Conference on Pervasive Computing and Applications (ICPCA)
2010 International Conference on E-Health Networking, Digital Ecosystems and Technologies (EDT)
2010 8th International Conference on Information & Communications Technologies (ICICT)
2010 International Conference on Computer Science and Software Engineering (CSSE 2010)
2010 Third International Symposiums on Electronic Commerce and Security (ISECS)
2010 Third International Conference on Education Technology and Training (ETT)
2010 Third International Symposium on Intelligent Information Technology and Security Informatics (IITSI)
2009 3rd International Conference on Genetic and Evolutionary Computing (WGEC)
2008 International Conference on Security Technology (SecTech 2008)
More links